How and Where to Find IT Vendors and Solutions
This guide helps you find IT vendors using online platforms like TechnologyMatch, G2, Clutch, Gartner Peer Insights, and Dark Social Reddit and Slack/Discord communities, so you can avoid lengthy sales processes.

The modern IT leader faces a paradox. You do not suffer from a lack of options. You suffer from an abundance of noise.
If you search for enterprise endpoint security today you will trigger an algorithmic avalanche. You will face thousands of search results and a barrage of retargeting ads. If you are careless enough to download a whitepaper you will face a sequence of cold calls from sales reps who don't like to take no for an answer.
For CIOs, CISOs, and Vice Presidents of Engineering the competency of vendor sourcing has shifted. It is no longer about finding a vendor. It is about filtering a saturated market to find the right partner without paralyzing your team or exposing your infrastructure to risk.
The cost of a poor selection is calculated in years rather than dollars. A mismatched ERP implementation or a failed MSP partnership results in technical debt. It leads to shadow IT proliferation and stalled digital transformation.
This guide details a rigorous and architectural approach to IT vendor discovery. It moves beyond generic listicles to provide a blueprint for using the specific discovery engines available to you in 2026. We will cover everything from curated marketplaces like TechnologyMatch to the private peer networks where your colleagues speak freely.
Defining The No-Regret Search Specification
Most sourcing failures occur before a single directory is opened. They happen because the search parameters are defined too loosely. This results in a long list of fundamentally mismatched entities.
Before you engage with the external market you must establish your No-Regret Criteria. These are the binary and non-negotiable attributes a vendor must possess to even warrant a conversation. This shifts your mindset from finding the best to eliminating the unfit.
Filter by Non-Functional Requirements First
Technical features are often similar across top-tier vendors. The true differentiators are usually non-functional attributes.
- Regulatory Compliance and Sovereignty: If you handle patient data a HIPAA-compliant tag is not a feature. It is a gatekeeper. If you are subject to GDPR the physical location of the data center is a hard filter. Do not waste cycles evaluating a tool that cannot legally house your data.
- Integration Ecosystem: Do not ask generic questions about integration. Ask specific and architectural questions. You need to know if there is a native and pre-built connector for your core stack in the AppExchange. If you need to build and maintain a custom API handler the total cost of ownership increases significantly.
- Operational Scale: A tool rated 5 stars by fifty freelancers is operationally useless to an enterprise with 5,000 seats. You must define the scale immediately to avoid tools that will buckle under your load.
The Buy vs. Build vs. Partner Sourcing Matrix
Your sourcing channel must change based on what you are buying. Using a software review site to find a consulting firm is a common error that leads to sub-optimal results.
Using TechnologyMatch for Curated and Private Discovery
Best For: High-stakes projects, privacy-conscious leaders, and accelerating the short list phase.
The traditional discovery model operates on a click-and-spam basis. You search for a solution and click a link. Your contact data is then sold to multiple vendors. TechnologyMatch inverts this model by operating as a buyer-led marketplace.
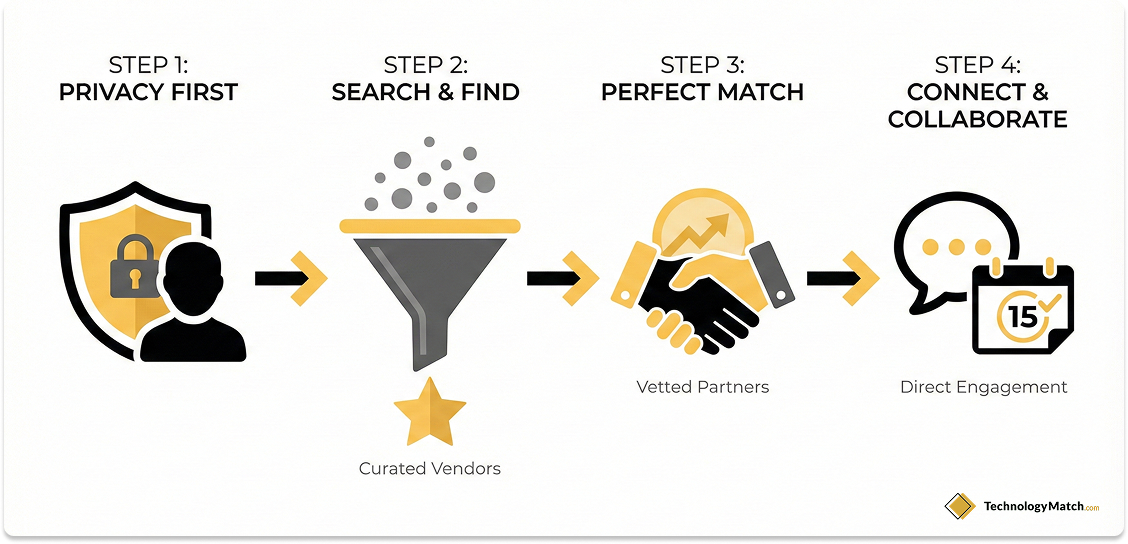
The Mechanics of Privacy-First Sourcing
TechnologyMatch solves the noise problem by keeping the IT buyer anonymous. You build a structured profile of your project needs. You specify budget, timeline, technical requirements, and compliance needs without revealing your identity.
Vendors on the platform can see the opportunity. They might see a mid-sized healthcare firm seeking an MSP with SOC 2 compliance. However they cannot see you. Crucially the vendor cannot contact you until you review their profile and accept the match. This puts you in total control of the engagement cadence.
Leveraging Vetted Vendor Networks
Unlike open directories where any company with an email address can create a listing, TechnologyMatch utilizes a vetting process. This is particularly valuable when sourcing Managed Service Providers or Value-Added Resellers. The platform verifies financial stability and certifications. This is often backed by data from major distributors. It ensures that the partners presented to you are solvent and capable of delivery. This pre-vetting saves your procurement team weeks of due diligence.
Leveraging G2 and Capterra for Broad Market Intelligence
Best For: Broad market scanning, identifying high performers, and competitive analysis.
G2 and Capterra are the volume engines of the industry. They rely on massive crowdsourced data to provide a real-time view of market sentiment. However to use them effectively you must learn to manipulate their filters to hide the noise.
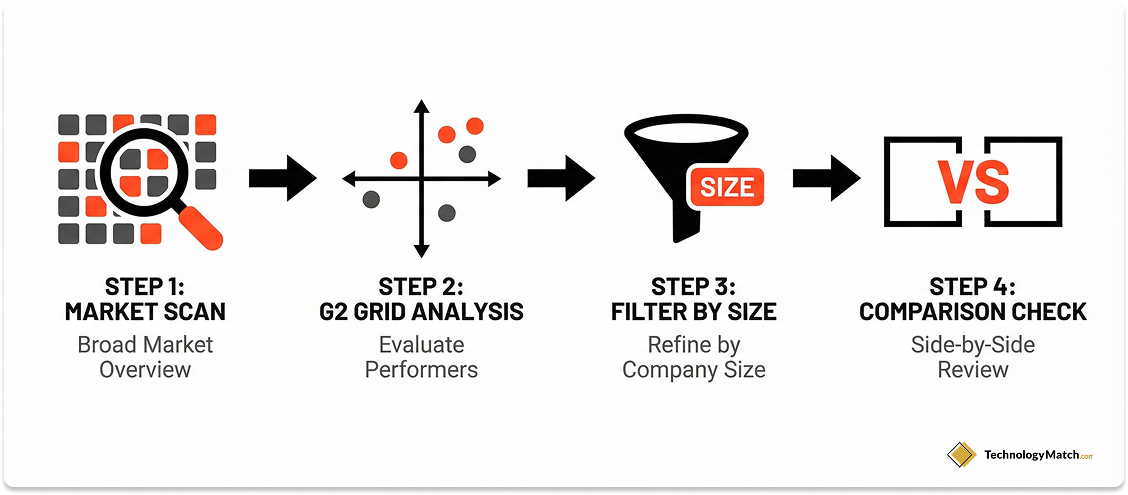
Analyzing the High Performer vs. Leader Quadrants
G2 uses a grid methodology to plot vendors on two axes. These are Market Presence and Customer Satisfaction.
- The Leader Trap: The top-right Leaders are safe bets. But they often come with enterprise price tags and slower innovation cycles. They also tend to have the largest marketing budgets for soliciting reviews.
- The High Performer Gold Mine: The top-left quadrant contains High Performers. These are vendors with high customer satisfaction but lower market presence. These are often the hidden gems. They are innovative challengers who are hungry for business. They offer better price-to-performance ratios and provide more attentive support than the incumbents.
Filtering for Enterprise Relevance
A 4.8-star rating is meaningless if it comes from a hobbyist. You must strip away irrelevant data.
- Company Size Filter: Immediately apply the Company Size > Enterprise filter. You will often see the rankings shift dramatically. A tool that is a Leader for SMBs might drop to a Niche player for enterprises because it lacks necessary governance features.
- Meets Requirements Metric: Sort vendors by the specific Meets Requirements score rather than the overall star rating. This is a stronger proxy for functional depth. It helps identify tools that are powerful but perhaps complex to use.
The Alternatives Page Hack
One of the fastest ways to build a long list is to search for the category leader. Search for Salesforce and navigate to its Alternatives page. This page is algorithmically populated with the direct competitors that other buyers have cross-shopped. It instantly provides a data-backed list of relevant vendors without requiring you to guess the correct category taxonomy.
Validating with Gartner Peer Insights
Best For: Enterprise-grade validation, Voice of the Customer reports, and board-level justification.
When your decision involves a multi-year contract and significant capital expenditure you need the gold standard of verification. Gartner Peer Insights differs from G2 in that it requires strict identity verification. This is usually done via corporate email. It significantly reduces the risk of fake or astroturfed reviews.
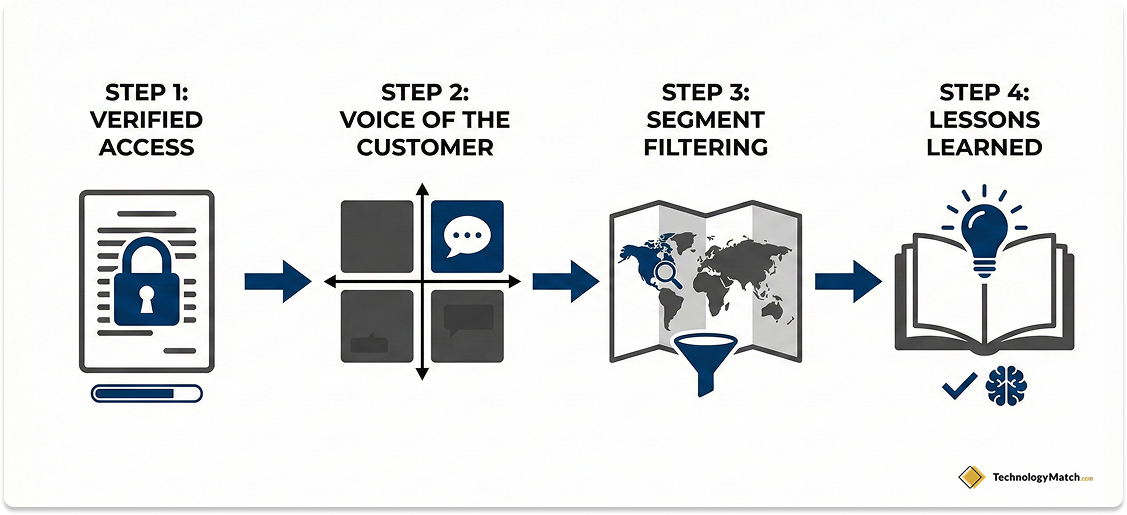
Using Segment Views to Remove Global Bias
A vendor might be a global leader in the Magic Quadrant but have zero support footprint in your specific region. Gartner Peer Insights offers Segment Views. These allow you to filter the Voice of the Customer quadrants by strictly defined parameters. You can filter by Industry, Company Size, and Region.
- Strategic Application: If you are a mid-sized German manufacturing firm use the Segment View to filter for Manufacturing and EMEA. This often reveals that a local European vendor outperforms the global US-based giants in your specific context. This is a nuance completely lost in the aggregate global view.
Mining Lessons Learned for Implementation Partners
Gartner Peer Insights asks reviewers to write about their lessons learned during implementation. This is a critical source of intelligence not just for the software but for the System Integrators.
- The Bank-Shot Strategy: Read the reviews for major platforms like SAP or Oracle. Reviewers often explicitly name the consultancy that helped them deploy the software. If a reviewer says the implementation was smooth thanks to a specific partner you have just found a vetted service provider. This allows you to build a list of recommended integrators who have proven expertise with that specific stack.
Sourcing Service Providers via Clutch and GoodFirms
Best For: Finding Managed Service Providers, Custom Development Shops, and Digital Agencies.
You cannot demo a service provider. You are buying a relationship. Clutch and GoodFirms are designed for this human capital discovery. They utilize metrics like hourly rates and verified project histories.
The Service Line Percentage Rule
A critical error IT leaders make is hiring a generalist. Clutch displays a Service Line chart for every vendor. This shows the percentage breakdown of their focus areas.
- The Rule: If you need a cybersecurity partner prioritize vendors where Cybersecurity constitutes more than 60% of their service line. Avoid vendors who show 10% in ten different categories. They are generalists and will likely lack the depth required for specialized threats.
Deciding on Hourly Rates and Project Size
Clutch provides explicit financial filters that help you frame the search within your budget constraints. Understanding the rate bands is essential for predicting quality.
- Under $25/hr (Offshore): High-volume execution. Good for staff augmentation but requires heavy management oversight.
- $50 - $99/hr (Nearshore/Boutique): The sweet spot for many. Good balance of cost and communication overlap. This often includes regions like Eastern Europe or Latin America.
- $150+/hr (Premium Onshore): Strategy-focused consultancies. Use them for architecture and roadmap design. Do not use them for routine ticket smashing.
Pro Tip: Filter by Minimum Project Size. If you are looking for a $1M transformation partner filter out vendors with a $5k minimum. They will not have the operational maturity or insurance to handle your contract.
Dark Social and Peer Validation Networks
Best For: Unfiltered truth, pricing transparency, and outage history.
The most valuable intelligence exists in dark social channels. These are private channels where candid discussions occur away from vendor marketing and public scrutiny.
Mastering Reddit for IT Due Diligence
Reddit has become a de facto review board for IT professionals. However you must know where to look.
- r/sysadmin and r/CIO: These communities are excellent for sanity checks on software stability. Search for Vendor X outage or Vendor Y price increase to see the raw history of the vendor’s performance. You will find horror stories and success stories that never make it to official case studies.
- r/msp: If you are sourcing a Managed Service Provider this subreddit is invaluable. It contains specific discussions on which master agents are reliable and which vendors are failing their partners.
The Strategic Value of r/ITManagers
While other subreddits focus on technical break-fix issues r/ITManagers is the gold mine for soft skill validation and contract negotiation tactics. This is where you go to vet the human element of the vendor relationship.
- Account Management Quality: Search this community to see how a vendor treats their clients after the ink is dry. You will find discussions on whether specific vendors are known for ghosting clients or nickel-and-diming for every change request.
- Contract Renewal Tactics: Users here often share specific details about renewal aggression. You might find threads warning that a specific vendor likes to hit clients with a 20% uplift at renewal if you don't give 90 days notice. This intelligence allows you to redline those clauses before you sign the initial contract.
- Peer-to-Peer Benchmarking: This is a safe space to ask about salary bands for new hires or reasonable costs for specific managed services. If you are quoted $150 per user for a service you can ask the community if that aligns with current market rates.
Search Strategy: Do not use Reddit’s internal search. Use Google with the site operator. For example: site:reddit.com/r/ITManagers "vendor negotiation tactics".
Specialized Slack and Discord Communities
For technical sourcing general forums are often too broad. Move to niche communities.
- MacAdmins Slack: The premier source for Apple device management vendors.
- CNCF Slack: The hub for Kubernetes and cloud-native vendors.
- Strategy: Join these workspaces and search their #vendor or #tools channels. The discourse here is peer-to-peer and highly technical. It is completely devoid of marketing fluff.
Advanced Search Engineering Techniques
Best For: Finding niche specialists and bypassing SEO-optimized landing pages.
Standard Google searches often yield only the most aggressive marketers. To find the actual experts you must use Boolean Logic to engineer your search strings.
The Negative Search Strategy
You can uncover hidden vendors by explicitly excluding the directory sites that clog up the first page of results.
- The Query:
(intitle:"managed services" OR intitle:"MSP") AND "healthcare" AND "SOC 2" -site:clutch.co -site:upcity.com - The Result: This forces Google to show you the actual websites of MSPs that specialize in healthcare and have SOC 2 compliance. It removes the aggregator sites from the results.
Resume Mining for Implementation Experts
Sometimes the best way to find a capable firm is to find the people who do the work.
- The Query:
site:linkedin.com/in "helped implement" AND "SAP S/4HANA" AND "retail" - The Strategy: This finds profiles of individuals who have successfully delivered the specific project you are planning. Look at their employment history. The consultancies they worked for are the ones you should be contacting. You are effectively reverse-engineering the talent pool.
The Tech Stack Scraping Method
If you admire a non-competitor's digital experience find out who they use.
- Tools: Use browser extensions like Wappalyzer or BuiltWith.
- Action: Go to the target company's website. The extension will instantly reveal their entire stack. You will see their CMS, their marketing automation platform, their analytics providers, and their CDNs. This gives you a proven recipe of compatible vendors that you can emulate.
Selection, Red Flags, and the POC
Once you have constructed your long list you must aggressively filter it down to a short list using a Request for Proposal or direct engagement.
The No-Go Red Flags
- The All-in-One Myth: Be extremely skeptical of vendors claiming to be leaders in five disparate categories. If a vendor says they do CRM, ERP, and Endpoint Security they are likely stretching the truth. In IT specialization usually beats generalization.
- Aggressive Lock-in Strategies: During your initial calls ask about data portability. If they cannot demonstrate a full-fidelity export of your data in a standard format like CSV or SQL dump they are planning to hold your data hostage. This is a disqualifying offense.
- Review Recency: Ignore a 4.8-star rating if the last review was from 2023. Software evolves rapidly. You need data from the last 12 months to judge current stability and support quality.
The Severity 2 Test During Proof of Concept
Never sign a multi-year contract based on a demo. Demand a scoped POC. During this period do not just test the features. You must test the support.
- The Test: File a Severity 2 ticket during the POC. This is a high-impact but non-critical issue.
- The Metric: Measure exactly how long it takes for a human to respond and how competent that first response is. You are not just buying software. You are buying the support team that stands behind it. If they are slow during the sales cycle they will be absent after the contract is signed.
Future Trends in Vendor Sourcing
The mechanisms of discovery are evolving rapidly. By 2026 we will see new filters and agents entering the sourcing workflow.
- AI-Driven Sourcing Agents: Procurement co-pilots are becoming standard. These internal AI agents ingest a company's requirements and autonomously scan the web to propose a long list. You must learn to prompt these agents effectively to get the best results.
- Sustainability as a Primary Filter: Green IT is moving from a PR metric to a hard search filter. Directories are beginning to include Carbon Footprint or Net Zero Commitment tags. Sourcing leaders in EMEA are increasingly using these filters to ensure their supply chain meets corporate ESG mandates.
Building a Defensible Sourcing Architecture
The paradox of choice is the defining challenge of the 2026 IT landscape. There are too many tools and too many vendors. There is simply too much noise.
However by adopting a structured sourcing architecture you can turn this abundance into an asset. Use TechnologyMatch to source anonymously and efficiently. Use G2 and Capterra to map the market landscape. Use Gartner Peer Insights to validate enterprise reliability. And finally verify everything in the Dark Social channels where your peers speak the truth.
The best vendor for your organization is not necessarily the one with the biggest booth at the conference. It is the one that aligns mathematically, technically, and culturally with your specific No-Regret criteria.
Looking for IT partners?
Find your next IT partner on a curated marketplace of vetted vendors and save weeks of research. Your info stays anonymous until you choose to talk to them so you can avoid cold outreach. Always free to you.
FAQ
How does TechnologyMatch differ from G2 or Capterra?
G2 and Capterra are open directories focused on review volume and visibility. They are often monetized by ads. TechnologyMatch is a curated marketplace that matches buyers with vendors based on specific project requirements. Crucially it keeps the buyer anonymous until they choose to engage. This protects them from unsolicited sales outreach.
What is the most effective way to validate a vendor's claims?
Beyond asking for case studies you should ask to speak with a current customer of a similar size and industry. Additionally check Gartner Peer Insights for Lessons Learned reviews. These often contain more candid details about the implementation realities than standard testimonials.
How do I find a specialized MSP for a niche industry?
Do not rely on general Top MSP lists. Use Clutch to filter by Industry Focus and Service Line. Additionally use Boolean search strings on Google to find specialists who may not be listed on the major directories. For example you can search for MSPs that specialize in dental and HIPAA.
Should I trust Leader quadrant vendors more than others?
Not necessarily. Leaders often have the highest market presence and marketing budgets but they can be expensive and slow to innovate. High Performers often offer better value and more personalized support. Always filter by your company size to see if a Leader is actually a leader for your specific segment.
What is the best non-functional filter to apply early in the search?
Integration Compatibility. Filter for vendors that have Native or Certified integrations with your core platforms like Salesforce or ServiceNow. Native implies a pre-built and maintained connection. Generic API access often requires you to build and maintain the middleware yourself.