What Are The Best IoT and Edge Computing Solution in 2025
IoT and edge computing require connectivity, security, and infrastructure working together. Compare providers for cellular IoT, Zero Trust security, edge colocation, and enterprise integration.
What to Look For in IoT and Edge Computing Solutions
IoT and edge computing require multiple integrated components, not single products. Success depends on selecting the right capabilities at each layer, especially for IT leaders.
Four critical layers:
- Connectivity: Reliable cellular/network access with multi-carrier redundancy and coverage validation
- Security: Zero Trust approaches with agentless protection for resource-constrained devices and network-level policy enforcement
- Edge infrastructure: Colocation facilities providing low-latency processing near deployment sites with proper power density and compliance certifications
- Integration: Expertise connecting IoT data to ERP, analytics, and business systems while maintaining network segregation
Four providers, four layers:NCG Networks handles device connectivity and telecom management. Zscaler Cellular secures cellular IoT with Zero Trust. CoreSite provides edge colocation. X10 Technologies integrates IoT and edge into broader IT environments.
We evaluate service models, geographic coverage, security frameworks, infrastructure capabilities, and proof requirements through scenario-based analysis. The goal: match your challenge to the right provider or combination, verify delivery in your environment, and confirm sustainable results.
Let’s get into the tools.
NCG Networks
Key Features
- IoT device procurement and provisioning for sensors, trackers, gateways, and edge devices
- Multi-carrier SIM provisioning and management with global coverage and carrier redundancy
- Flexible data plans optimized for IoT, including pay-as-you-go, pooled data, and enterprise contracts
- IoT asset tracking for vehicles, equipment, containers, and high-value assets
- Environmental monitoring sensors for temperature, humidity, air quality, and facility conditions
- Remote automation and control for industrial equipment and building management
- Vendor-agnostic device selection based on use case requirements
Considerations
NCG is a connectivity and device procurement specialist, not an IoT platform or application vendor. You'll need separate software for data visualization, analytics, and business logic. Multi-carrier strategies require validation of actual coverage in your deployment locations.
Pros
Simplifies IoT device procurement and connectivity management under one vendor. Multi-carrier approach provides redundancy and coverage optimization. Flexible data plans reduce costs for variable IoT deployments. Telecom expertise navigates carrier contracts and global roaming. Vendor-agnostic device selection ensures fit-for-purpose hardware.
Cons
Not an IoT platform. Requires separate analytics and application software. Multi-carrier management adds complexity if not properly governed. Limited public information on security features and platform integrations.
Best Suited For
Organizations deploying IoT sensors, trackers, and edge devices across multiple locations needing simplified connectivity management, multi-carrier redundancy, and vendor-agnostic device procurement.
Evaluation questions for the vendor
- What's your device procurement process including lead times and certification?
- How do you manage multi-carrier SIM provisioning and failover for redundancy?
- What data plan options optimize costs for our usage patterns?
- What coverage validation do you provide for our specific deployment locations?
- How do you integrate with IoT platforms and device management systems?
- Can you provide case studies in our industry with similar device types and scale?
Zscaler Cellular
Key Features
- Zero Trust security for cellular-connected IoT devices, mobile workforces, and remote assets
- Agentless security requiring no software installation on devices
- SIM-based traffic steering routing all cellular traffic through Zscaler cloud security platform
- Policy enforcement for application access, data protection, and threat prevention
- Real-time anomaly detection and threat intelligence for cellular traffic
- Global coverage with 150+ data centers ensuring low-latency security inspection
- 100% traffic visibility for all cellular-connected devices regardless of location
- Eliminates attack surface by making devices invisible and enforcing least-privilege access
Considerations
Zscaler Cellular is a security solution, not a connectivity provider or IoT platform. You still need cellular carriers and SIM cards. Requires SIM-based traffic steering, which may need carrier coordination. Pricing model and SIM compatibility should be validated early.
Pros
Agentless deployment eliminates software management on resource-constrained IoT devices. SIM-based approach works with any cellular device without modification. Zero Trust model prevents lateral movement and reduces attack surface. Real-time threat detection protects against compromised devices. Global coverage ensures consistent security regardless of device location. Strong fit for regulated industries requiring cellular device security.
Cons
Requires SIM-based traffic steering which may need carrier coordination or SIM replacement. Not a connectivity provider. Limited public information on pricing and deployment timelines. May add latency for latency-sensitive IoT applications.
Best Suited For
Enterprises securing cellular-connected IoT devices including fleet telematics, point-of-sale systems, industrial sensors, kiosks, and mobile workforces with Zero Trust security and policy enforcement.
Evaluation questions for the vendor
- How does SIM-based traffic steering work and what SIM types are compatible?
- What's the deployment process including carrier coordination?
- How do you handle latency-sensitive IoT applications?
- What policy controls are available for IoT device segmentation?
- How do you integrate with existing security tools?
- What visibility and reporting do you provide for cellular IoT traffic and threats?
- What's your pricing model and how does it scale with device count?
CoreSite
Key Features
- High-performance colocation in strategic U.S. markets including Los Angeles, Silicon Valley, Denver, Chicago, Boston, New York, Northern Virginia, and Miami
- Low-latency interconnection with 475+ network providers and cloud onramps
- Direct cloud onramps to AWS, Azure, Google Cloud, Oracle Cloud, and IBM Cloud
- Carrier-neutral facilities providing choice and redundancy
- Scalable power and space from single cabinets to multi-megawatt deployments
- 99.999% uptime SLA with redundant power, cooling, and network infrastructure
- Edge colocation for latency-sensitive applications including IoT data processing and AI inference
- Compliance certifications including SOC, PCI-DSS, HIPAA, and FISMA
Considerations
CoreSite provides physical infrastructure, not IoT platforms or connectivity services. You'll need to bring or procure servers, networking equipment, and software. Colocation requires upfront capital expenditure or leasing. Geographic coverage is U.S.-focused. Best for organizations with predictable, high-performance workloads requiring low latency.
Pros
Strategic locations near major network exchange points minimize latency for edge workloads. Dense network ecosystems provide connectivity choice. Direct cloud onramps simplify hybrid architectures for IoT data pipelines. Carrier-neutral model prevents vendor lock-in. High uptime SLAs support mission-critical IoT applications. Scalable infrastructure accommodates growth. Strong compliance certifications for regulated industries.
Cons
Physical infrastructure only. Requires separate hardware, software, and connectivity procurement. U.S.-focused geographic coverage. Colocation model requires capital expenditure. May be overkill for small-scale or pilot IoT deployments.
Best Suited For
Organizations needing physical edge infrastructure to host IoT data processing, AI inference, real-time analytics, and low-latency applications in strategic U.S. markets with high uptime and compliance requirements.
Evaluation questions for the vendor
- What's the latency from your facilities to our key IoT deployment locations?
- What network providers and cloud onramps are available in the markets we need?
- What power densities do you support for high-performance compute?
- What compliance certifications do you provide for our industry?
- What remote hands and managed services are available?
- How do you handle scalability from pilot to production-scale infrastructure?
- Can you provide case studies for IoT or edge computing workloads in our industry?
X10 Technologies

Key Features
- IT solutions integration across cybersecurity, networking, cloud, and infrastructure
- Technology assessment and strategic planning for IT modernization
- Network design and implementation for enterprise, campus, data center, and edge environments
- Cybersecurity solutions including Zero Trust, endpoint protection, and network security
- Cloud migration and hybrid cloud architecture for AWS, Azure, and Google Cloud
- Managed services for ongoing IT operations, monitoring, and support
- Vendor partnerships with Aruba, Fortinet, IBM, Cisco, Dell, and HPE
- Cross-domain expertise integrating IoT, edge, cloud, and enterprise systems
Considerations
X10 is a broad IT solutions integrator. IoT and edge computing are part of a larger portfolio, not the primary focus. Best leveraged for strategic initiatives requiring integration across multiple technology domains. Less specialized in pure-play IoT platforms compared to focused vendors.
Pros
Cross-domain expertise integrates IoT and edge solutions with enterprise networking, security, and cloud infrastructure. Strategic consulting aligns technology investments with business objectives. Vendor-agnostic partnerships provide flexibility. Managed services provide ongoing operations for complex IT environments.
Cons
Less specialized in IoT platforms and edge computing compared to pure-play vendors. Broader consulting model may have higher costs for straightforward IoT deployments. Limited public information on specific IoT case studies.
Best Suited For
Organizations seeking strategic IT consulting and integration to connect IoT and edge solutions with enterprise networking, security, cloud, and data systems as part of broader IT modernization.
Evaluation questions for the vendor
- What's your experience with IoT and edge computing implementations in our industry?
- How do you approach integration of IoT data with enterprise systems?
- What network architecture do you recommend for edge computing and IoT connectivity?
- How do you integrate edge security with broader Zero Trust frameworks?
- What managed services do you offer for ongoing IoT and edge operations?
- Can you provide reference cases showing IoT deployments integrated with enterprise IT?
Which IoT and Edge Computing Tool to Use In Which Scenario?
Scenario 1: Fleet Tracking and Telematics
Challenge: Track vehicles across multiple regions, monitor driver behavior, optimize routes, and prevent theft. Requires cellular connectivity, real-time data processing, and security to protect operational data.
Best Fit: NCG Networks + Zscaler Cellular + CoreSite
NCG provides multi-carrier SIM provisioning for nationwide coverage and GPS tracker procurement. Multi-carrier approach ensures connectivity in remote areas. Zscaler secures all cellular traffic with Zero Trust policies, preventing compromised trackers from becoming network entry points. CoreSite hosts edge processing for real-time route optimization with low-latency access to fleet management platforms.
Why this works: Connectivity ensures devices stay online. Security protects sensitive data. Edge infrastructure enables real-time decision-making without cloud round-trip latency.
Scenario 2: Manufacturing IoT and Predictive Maintenance
Challenge: Deploy sensors on factory equipment to monitor vibration and temperature. Use predictive analytics to prevent downtime. Requires low-latency processing and integration with MES and ERP systems.
Best Fit: NCG Networks + CoreSite + X10 Technologies
NCG provides industrial-grade sensors and cellular connectivity for factory environments. CoreSite hosts edge compute near manufacturing facilities for real-time predictive analytics and AI models. X10 integrates sensor data with manufacturing execution systems and ERP platforms, designs secure network architecture segregating OT from IT, and provides managed services.
Why this works: Connectivity gets sensor data flowing. Edge infrastructure processes data with minimal latency. Integration connects IoT insights to business systems.
Scenario 3: Retail IoT for Point-of-Sale and Kiosks
Challenge: Secure cellular-connected POS terminals and kiosks across hundreds of retail locations. Requires real-time transaction processing and protection against payment card theft.
Best Fit: Zscaler Cellular + CoreSite + NCG Networks
Zscaler secures cellular-connected POS devices and kiosks with agentless Zero Trust. Critical for PCI-DSS compliance and protecting payment card data. CoreSite provides regional edge infrastructure for customer analytics and inventory management. NCG provides backup connectivity for stores with unreliable primary internet.
Why this works: Security protects payment systems. Edge infrastructure enables real-time customer experiences. Backup connectivity ensures business continuity.
Scenario 4: Smart Building and Facility Management
Challenge: Monitor and control HVAC, lighting, and access control across multiple facilities. Optimize energy usage and enable predictive maintenance for building systems.
Best Fit: NCG Networks + X10 Technologies
NCG provides environmental monitoring sensors and remote automation for HVAC and lighting control. X10 integrates building automation systems with enterprise IT, designs network architecture segregating building systems from corporate networks, and implements cybersecurity controls.
Why this works: Sensors provide real-time building data. Integration connects building systems to enterprise platforms and ensures security.
Scenario 5: Healthcare IoT and Remote Patient Monitoring
Challenge: Deploy medical-grade IoT devices for remote patient monitoring and asset tracking. Requires HIPAA compliance, high reliability, and secure connectivity.
Best Fit: NCG Networks + Zscaler Cellular + CoreSite
NCG provides medical-grade IoT devices and cellular connectivity for remote patient monitoring. Zscaler secures cellular-connected medical devices for HIPAA compliance and protects patient health information. CoreSite provides HIPAA-compliant edge infrastructure for processing patient data with low latency and high availability.
Why this works: Medical-grade connectivity ensures device reliability. Security protects patient data and ensures compliance. Edge infrastructure enables real-time patient monitoring.
Takeaways For Better Decision-Making
IoT and edge computing are a stack, not a single solution. Think in layers. Connectivity gets devices online. Security protects traffic and endpoints. Edge infrastructure hosts workloads close to data sources. Integration ties IoT data into enterprise systems. Most deployments need multiple layers.
Start with connectivity and security, then add edge compute as workloads grow. NCG and Zscaler can be deployed quickly. CoreSite edge infrastructure makes sense when you have predictable, high-performance workloads requiring low latency. Pilot deployments often start with cloud-based processing and migrate to edge as scale increases.
Multi-carrier strategies provide redundancy but add complexity. NCG's multi-carrier approach prevents single points of failure for critical IoT deployments. Essential for fleet tracking and remote monitoring where connectivity loss means business disruption.
Zero Trust is essential for cellular IoT security. Cellular-connected devices are often overlooked in security strategies. Zscaler's agentless approach solves the challenge of securing resource-constrained devices. Critical for regulated industries and compliance requirements.
Edge infrastructure decisions depend on latency and data volume. CoreSite makes sense when round-trip latency to cloud exceeds application requirements or when data volumes make cloud backhaul expensive. Pilot in cloud first, then migrate to edge when performance or cost justifies infrastructure investment.
Integration expertise prevents IoT silos. X10 addresses the common challenge of IoT data sitting in isolated systems. Integration with ERP and analytics platforms unlocks business value. Security integration ensures IoT doesn't create new attack vectors.
Validate coverage and latency in your actual deployment locations. Carrier coverage maps are optimistic. NCG's coverage validation reduces deployment risk. For CoreSite, measure actual latency from facilities to your IoT deployment locations.
Measure outcomes, not just device counts. Track uptime, security incidents, latency, cost per device, and business outcomes like operational efficiency and downtime reduction. Require proof of measurable results in pilots before full-scale deployment.
How Can You Work With These Vendors Through TechnologyMatch
IoT and edge computing require layered solutions addressing connectivity, security, infrastructure, and integration. No single vendor covers all layers.
NCG Networks connects devices with multi-carrier redundancy. Zscaler Cellular secures cellular traffic with Zero Trust. CoreSite hosts edge workloads with low latency. X10 Technologies integrates IoT solutions with enterprise systems.
Your IoT and edge challenge determines which layers you need and which providers to engage. Match providers to your requirements, verify delivery in your environment, and confirm you can sustain results.
Here’s how you can explore these vendors on the TechnologyMatch platform:
1. After you signup to TechnologyMatch, search for “IoT” or “Edge Computing” on the dashboard.
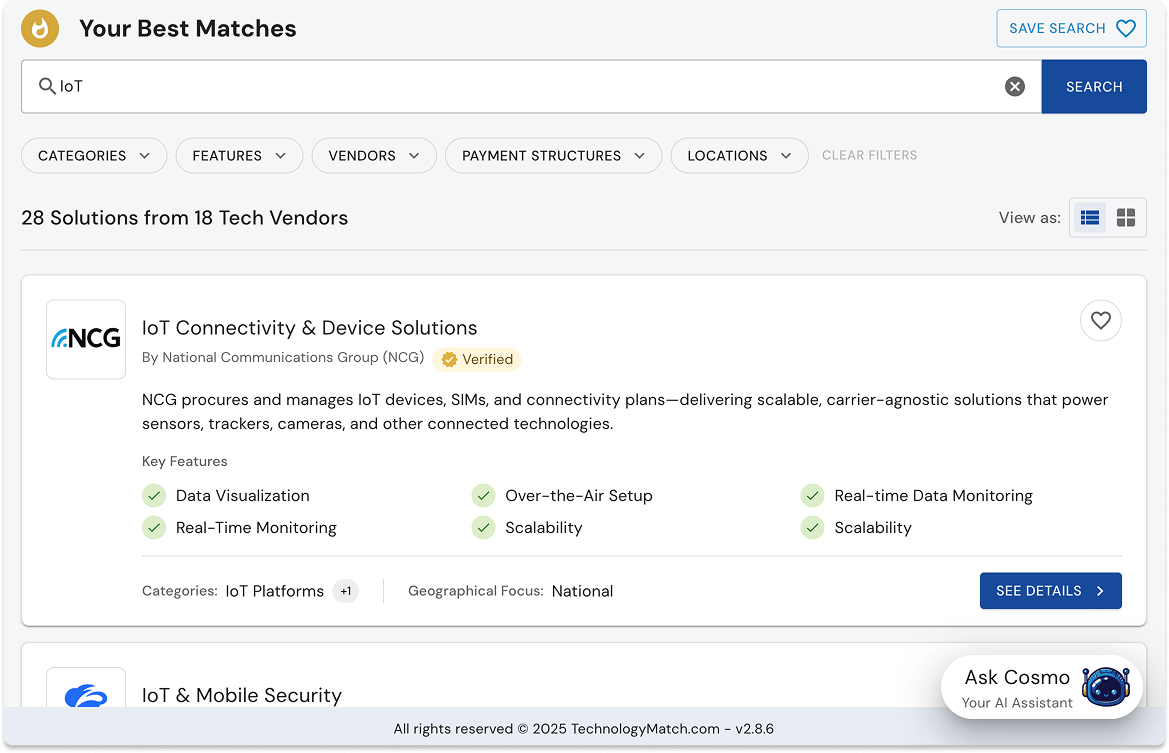
2. Navigate through the solution providers and their offerings. Accept Match with the potential partner or vendor.
3. The new match will show up in the “My Matches” section of your dashboard. You can now message them or schedule a meeting. The meeting then shows up in your calendar.

We know how difficult it is to find and work with the right partners in the market today. There’s too much noise and not enough reliable solution providers. Which is why we built TechnologyMatch:
- Our platform is buyer-first so potential partners have no way of spamming with you cold outreach.
- Only you can make the first move by messaging them and scheduling calls.
- All your potential partners can be managed and evaluated from a single dashboard, without having to switch platforms or sift through emails.
- You get access to potential partners, resellers, vendors, and solution providers who have been verified through a strict vetting process.
Looking for IT partners?
Find your next IT partner on a curated marketplace of vetted vendors and save weeks of research. Your info stays anonymous until you choose to talk to them so you can avoid cold outreach. Always free to you.
FAQ
What IoT connectivity services does NCG Networks provide?
NCG Networks provides IoT device procurement, multi-carrier SIM provisioning and management with global coverage, flexible data plans optimized for IoT use cases, IoT asset tracking for vehicles and equipment, environmental monitoring sensors, remote automation and control capabilities, and vendor-agnostic device selection based on use case requirements.
How does Zscaler Cellular secure IoT devices?
Zscaler Cellular provides Zero Trust security for cellular-connected IoT devices using agentless, SIM-based traffic steering that routes all cellular traffic through Zscaler's cloud security platform. It enforces policies for application access and data protection, provides real-time anomaly detection, offers 100% traffic visibility, and eliminates attack surface by making devices invisible to the internet.
What edge computing infrastructure does CoreSite offer?
CoreSite provides high-performance colocation in strategic U.S. markets with low-latency interconnection to 475+ network providers, direct cloud onramps to AWS, Azure, Google Cloud, Oracle, and IBM Cloud, carrier-neutral facilities with scalable power and space, 99.999% uptime SLA, and compliance certifications including SOC, PCI-DSS, HIPAA, and FISMA.
How does X10 Technologies integrate IoT with enterprise systems?
X10 Technologies provides IT solutions integration including technology assessment, network design for enterprise and edge environments, cybersecurity solutions with Zero Trust frameworks, cloud migration and hybrid architecture, managed services for ongoing operations, and cross-domain expertise integrating IoT and edge solutions with enterprise networking, security, cloud infrastructure, and business systems.
What are the key layers of an IoT and edge computing deployment?
IoT and edge deployments require four key layers. Connectivity layer gets devices online with cellular or private networks. Security layer protects device traffic with Zero Trust policies. Infrastructure layer hosts edge workloads for low-latency processing near data sources. Integration layer connects IoT data to enterprise systems like ERP and analytics platforms for operational value.