The manufacturing IT Leader's no-BS guide to OT/IT convergence that actually works
There's a strong disconnect between IT and operations on the manufacturing front but these departments are 2 of the most important when it comes to breaking down silos and streamlining functionality. Converging OT/IT is an important step towards enabling business success but the process itself can be effort-intensive. This guide gives you a framework to seamlessly integrate these functions together.
It’s difficult to make some components work
Managing IT in the manufacturing industry is hard. Unlike your peers in other industries, you're navigating two fundamentally different technological worlds that were never designed to work together. This isn't just a technical challenge, it's a daily operational reality that shapes every decision you make.
The "Jenga Problem"
You're living with what one manufacturing IT director aptly called "the Jenga problem." Your production environment runs on systems where:
- Critical OT components have 15-30 year lifecycles while your IT refresh cycle is 3-5 years.
- 67% of your integration challenges stem from legacy systems that were never designed for connectivity (IDC, 2024).
- Every modification risks cascading failures across dozens of interdependent systems.
This isn't merely inconvenient, it's existentially risky. As you've likely experienced, changing one field in a core manufacturing system can affect "48 downstream reports," each requiring validation before you can proceed. Unlike your peers in tech companies who can rebuild from scratch, you must maintain production continuity while modernizing systems that directly impact your company's ability to manufacture products.
The documentation challenge compounds this problem. According to Gartner (2024), 58% of manufacturing environments operate with incomplete or outdated OT documentation. You're essentially performing surgery on systems you can't fully see.
The operational-security paradox
The convergence of previously isolated OT systems with your IT networks has created a security landscape unlike any other industry:
- 75% of manufacturing cyber incidents now involve converged IT/OT systems, up from 47% in 2021 (Infosecurity Magazine, 2024).
- Manufacturing has become the #1 target for ransomware, specifically because attackers know your production systems can't afford downtime.
- The average cost of downtime in manufacturing is now $260,000/hour (Aberdeen, 2023).
You face a daily paradox: production demands connectivity for efficiency, while security demands isolation for protection. Unlike purely digital businesses, security failures in your environment don't just leak data—they can physically stop production lines, damage equipment, or even create safety hazards.
The reality is that your OT networks were designed for reliability, not security. Many of your controllers, PLCs, and SCADA systems use proprietary protocols that predate modern security concepts entirely. You're trying to retrofit security into systems that were architected without it, often with limited vendor support for older but critical components.
Different culture, different priorities
Perhaps your most challenging daily reality is bridging the profound cultural gap between IT and OT teams. While IT values change, innovation, and standardization, OT prioritizes stability, uptime, and process continuity.
This isn't a personality conflict, it's a fundamental difference in mission. Your OT engineers have been trained that a minute of downtime costs thousands in lost production. They've developed a deep skepticism of anything that might disrupt stable operations. Meanwhile, your IT teams are pushing for security patches, cloud integration, and standardized platforms.
As an IT leader in the manufacturing industry, you most probably have to speak two different languages on the same day. With the OT team, you discuss uptime and reliability, and with the IT team, you talk about security and scalability. You have to constantly translate between worlds that have completely different definitions of success.
This divide extends to organizational structure. In 67% of manufacturing companies, IT and OT report through entirely different chains of command (Gartner, 2024). You're likely responsible for integrating systems that are ultimately controlled by different executives with different priorities and performance metrics.
Real-time data integration
The greatest untapped potential in your environment is the ability to make data-driven decisions using real-time operational information:
- Manufacturing companies with integrated IT/OT data environments achieve 15-20% higher OEE and 30% lower unplanned downtime (IoT Analytics, 2024)
- Yet only 12% of manufacturers have achieved "enterprise-scale" AI/ML deployment across IT/OT boundaries (IDC, 2024)
The challenge isn't just technical, it's structural. Your operational data is trapped in isolated systems, often requiring manual extraction and processing before it can inform decision-making. By the time information from the production floor reaches enterprise systems, the opportunity to make real-time interventions has passed.
This data fragmentation directly impacts your ability to implement predictive maintenance, quality optimization, and energy efficiency initiatives—all of which require seamless data flow between operational and information systems.
Skill gaps and lack of expertise
You're facing a critical skills shortage that compounds all other challenges:
- 82% of manufacturing IT leaders report difficulty finding talent with both IT and OT expertise (Deloitte, 2024)
- The most experienced OT engineers are approaching retirement age, taking irreplaceable knowledge with them
- Modern IT specialists rarely have experience with industrial protocols and operational constraints
Unlike in tech companies, where talent can focus on leading-edge technologies, your teams need to maintain both legacy industrial systems and modern IT platforms simultaneously. You're competing for security talent against financial services firms that can offer higher compensation, while also needing specialized knowledge in industrial control systems that few cybersecurity professionals possess.
The cost of silos
The financial impact of maintaining disconnected IT and OT environments is increasingly untenable:
- 28% higher technology TCO compared to companies with integrated approaches (Deloitte, 2024)
- 37% more unplanned downtime directly impacting production capacity (McKinsey, 2024)
- 3.2x higher risk of significant cybersecurity incidents (IBM, 2024)
- Limited ability to implement the Industry 4.0 initiatives that your executive team is demanding
You're caught in a challenging position: executives expect digital transformation and OT/IT convergence, but may not fully appreciate the complexity involved or provide adequate resources. As BCG (2024) notes, while approximately 10% of greenfield manufacturing projects implement converged IT/OT technologies today, this is expected to reach 50% within five years, creating pressure to adapt quickly despite all constraints.
Why converge OT/IT?
Your guardian instincts prioritize system reliability and production continuity. OT/IT convergence directly supports this protective mission with measurable outcomes. Apparently, companies have seen 15-20% improvement in Overall Equipment Effectiveness (OEE) through real-time monitoring and predictive intervention (IoT Analytics, 2024).
There’s also been about a 30% reduction in unplanned downtime by identifying equipment issues before they cause failure, and a 22% decrease in mean-time-to-repair (MTTR) when maintenance teams have integrated access to both operational and IT data.
These aren't abstract metrics—they translate directly to production capacity, delivery reliability, and bottom-line performance. IT leaders and directors have identified patterns that have helped them prevent a class of failures costing about $450,000 annually in scrapped materials and downtime after integrating their OT data with our ERP and analytics platforms.
For your protector identity, this represents the ultimate win: improved stability and reliability through strategic technological evolution. You're not changing for change's sake—you're strengthening the foundation that production depends on.
Disconnected systems keeping you up at night?
The security implications of disconnected systems likely keep you up at night—a legitimate fear given the rising threats to manufacturing. Your concerns about catastrophic blame following a breach are well-founded, but convergence offers a path to greater control:
- Comprehensive visibility across previously isolated systems, eliminating blind spots where threats can hide.
- Consistent security controls applied across both domains, reducing the risk of lateral movement during attacks.
- Coordinated incident response that addresses both IT and OT components of security events.
Some IT leaders have reportedly had to manage two separate security teams looking at different parts of the same attack. But with unified monitoring and response, they can detect something suspicious and immediately see if it's affecting both environments and respond accordingly.
This unified approach directly addresses the impostor syndrome that many manufacturing IT leaders experience around security. Rather than feeling caught between IT security standards and OT operational requirements, you can implement a cohesive strategy that respects both domains' legitimate needs.
Real-time, actionable data
While your protector side focuses on stability, your visionary identity seeks opportunities for transformation. Integrated OT/IT environments create a foundation for innovation that wasn't possible in siloed operations. According to a report by McKinsey, predictive maintenance reduces parts inventory by 15-30% while improving machine availability. The quality of data is optimized through real-time process adjustments based on integrated data analysis.
The amount of energy consumed is reduced by 10-20% through automated monitoring and control systems. The supply is made more visible, connecting production status directly to customer commitments.
These capabilities aren't just technological achievements, they're competitive advantages in markets where efficiency and responsiveness increasingly determine success. IT leaders across the manufacturing industry have discovered process variations that were causing inconsistent product quality after connecting their production data directly to the analytics platform. These fixes saved over $2 million annually in returns and rework.
For your innovator identity, this data integration creates a playground for meaningful transformation that delivers tangible business results, reinforcing your role as a strategic partner rather than just a technology manager.
Compliance readiness is important
The relationship-focused aspect of your leadership understands that compliance isn't just about avoiding penalties. It's about building trust with regulators, customers, and executives. Integrated OT/IT environments significantly streamline compliance efforts through:
- Automated documentation of security controls, configurations, and changes across both environments.
- Consistent policy application that satisfies requirements from NIST, IEC 62443, and industry-specific regulations.
- Simplified audit processes with comprehensive visibility into all technology assets.
- Proactive risk management that identifies and addresses compliance gaps before they become findings.
This compliance efficiency addresses a key pain point—the documentation burden that consumes 18-25% of IT teams' time in regulated environments (LNS Research, 2024). By reducing this overhead, you free resources for more strategic work while strengthening your reputation as a reliable steward of critical systems.
Collaboration and transparency
Creating a unified technological environment requires shared metrics balancing uptime, security, innovation, and efficiency; cross-functional teams appreciating both IT and OT priorities; unified leadership making holistic technology decisions; and a common language bridging previously siloed groups. Together, these elements create a cohesive approach where technology comprehensively serves business objectives.
This integration addresses the fundamental tension many manufacturing IT leaders experience—the feeling of being caught between worlds, never fully belonging to either IT or operations. Disconnected and siloed IT leaders find themselves constantly code-switching between languages and priorities. With an integrated team with shared goals, it becomes easier to lead with without having to divide yourself amongst teams.
Bridging the gap between operations and finances
Your role requires translating technical realities into business language. The financial impact of OT/IT convergence provides compelling arguments for executive support:
- 20-30% average ROI within 3 years of implementation (Boston Consulting Group, 2024).
- 15-20% reduction in total cost of ownership for technology infrastructure through the elimination of redundant systems and improved resource utilization.
- 7-12% improvement in manufacturing throughput through optimized processes and reduced downtime.
- Significant risk reduction in an environment where the average cost of a cyber breach in manufacturing has reached $4.35 million (IBM, 2023).
These figures aren't theoretical—they're being achieved by manufacturers who have successfully navigated the convergence journey. They provide the business justification that aligns your technical vision with executive priorities, strengthening your position as a strategic business partner.
The OT/IT convergence framework: A step-by-step guide
Let's cut through the complexity with a practical, tested approach to OT/IT convergence. This framework isn't theoretical—it's built from the trenches of manufacturing technology integration, designed to give you clear action steps while respecting the operational realities you face daily.
Step 1: Baseline assessment – Know where you stand
Start with a comprehensive inventory of your current state. You can't improve what you can't measure, and you can't secure what you can't see.
Key Actions:
- Asset Discovery and Mapping
- Deploy automated discovery tools (Claroty, Nozomi, Cisco Cyber Vision) to identify all OT assets
- Document all PLCs, HMIs, RTUs, historians, and control systems with firmware versions
- Target >95% visibility of all OT devices—a critical baseline for both security and integration
- Network Architecture Review
- Map existing network segments, trust boundaries, and data flows between OT and IT
- Identify "flat" networks where segmentation is needed
- Document all connection points between OT and IT environments, including any "shadow IT" bridges
- Performance Metrics Collection
- Establish your baseline OEE, downtime frequency/duration, and mean time to repair (MTTR)
- Document current data latency (how long it takes for shop floor data to reach enterprise systems)
- Catalog recent security incidents, near-misses, and audit findings
- Skills and Process Assessment
- Evaluate current team capabilities across both IT and OT domains
- Document existing maintenance, change management, and incident response procedures
- Identify overlaps and gaps between IT and OT processes
Practical Tip: "Don't boil the ocean. Start with your most critical production line or plant—one where you have good relationships with operations and where improvements would deliver significant business value." – Manufacturing IT Director, Automotive Sector
Output: Comprehensive baseline report with asset inventory, network diagrams, performance metrics, and process documentation. This becomes your reference point for measuring progress.
Step 2: Assemble a cross-functional team
Success depends on bringing the right people together early. This isn't just about technology—it's about aligning people with different priorities, vocabularies, and risk tolerances.
Key Actions:
- Core Team Formation
- IT networking/security specialists
- OT/plant floor engineers and technicians
- Process engineers who understand production workflows
- Compliance/regulatory representatives
- Safety personnel (particularly in hazardous environments)
- Key vendor partners for critical systems
- Ownership and Governance
- Create a RACI matrix defining who's Responsible, Accountable, Consulted, and Informed for each aspect of convergence
- Establish clear decision rights—who can approve changes to which systems
- Define escalation paths for conflicts or high-risk decisions
- Communication Protocols
- Set regular meeting cadence (weekly for core team, monthly for steering committee)
- Establish tools and channels for cross-team collaboration
- Create a common vocabulary that bridges IT and OT terminology
- Education and Alignment
- Conduct cross-training sessions on IT security fundamentals for OT staff
- Provide OT process and safety training for IT personnel
- Establish shared understanding of business priorities and constraints
Practical Tip: "We created a 'diplomat' role—someone with experience in both worlds who could translate between IT and OT teams. This person became invaluable in resolving conflicts and ensuring both sides felt heard." – IT Operations Manager, Chemical Manufacturing
Output: Defined team structure, RACI matrix, meeting schedule, and communication plan. This creates the human infrastructure necessary for successful integration.
Step 3: Set measurable goals and build a roadmap
Establish clear, measurable objectives linked to business outcomes. This creates alignment, enables progress tracking, and helps justify the necessary investments.
Key Actions:
- Define Business-Aligned KPIs
- Asset visibility target (>95% of OT devices mapped and monitored)
- Network monitoring coverage (>80% of OT traffic monitored)
- Patch management efficiency (<30 days to remediate critical vulnerabilities)
- OEE improvement target (+5% within 12 months)
- Downtime reduction goal (-20% unplanned downtime)
- Incident response integration (100% of IR playbooks include both IT and OT)
- Cross-training metrics (>80% of staff trained across domains)
- Compliance targets (zero critical audit findings)
- Build a Phased Roadmap
- Phase 1 (0-3 months): Visibility and monitoring
- Phase 2 (3-6 months): Segmentation and secure connectivity
- Phase 3 (6-12 months): Data integration and analytics
- Phase 4 (12-18 months): Advanced capabilities (predictive maintenance, etc.)
- Resource Planning
- Identify required tools, technologies, and services
- Determine staffing needs and skills gaps
- Develop training plans for existing team members
- Create budget estimates for each phase
- Risk Assessment
- Identify potential production impacts during implementation
- Develop mitigation strategies for each identified risk
- Create rollback plans for critical changes
Practical Tip: "Be ruthlessly realistic in your timeline. In manufacturing environments, everything takes longer than you expect due to production constraints, change windows, and the need for extensive testing. Build in buffer time and set expectations accordingly." – IT Director, Food & Beverage Manufacturing
Output: Documented KPIs, phased roadmap with milestones, resource plan, and risk assessment. This creates the strategic framework for your convergence journey.
Step 4: Pilot and measure
Begin with a controlled implementation that delivers tangible value while minimizing risk. This builds credibility, generates lessons learned, and creates momentum for broader rollout.
Key Actions:
- Pilot Site Selection
- Choose a representative production line, cell, or plant
- Select an area with supportive operations leadership
- Ensure the scope is manageable but meaningful
- Implementation
- Deploy asset discovery and monitoring tools
- Implement appropriate network segmentation
- Establish secure data flows between OT and IT systems
- Develop and test integrated incident response procedures
- Data Collection
- Measure before/after metrics for all defined KPIs
- Track implementation challenges and solutions
- Document any production impacts (positive and negative)
- Gather feedback from both IT and OT personnel
- Adjustment
- Refine approaches based on lessons learned
- Address any technical or procedural gaps
- Update the roadmap and resource plans if needed
Practical Tip: "We found it valuable to create a 'digital twin' of our pilot area—a test environment where we could validate changes before implementing them in production. This reduced risk and built confidence with operations teams." – IT Infrastructure Manager, Aerospace Manufacturing
Output: Pilot implementation report with measured results, lessons learned, and recommendations for broader deployment. This provides evidence-based validation for your approach.
Step 5: Review, benchmark, and improve
Establish a cycle of continuous improvement that builds on early successes while adapting to changing requirements and emerging technologies.
Key Actions:
- Quarterly Reviews
- Compare current metrics against baseline and targets
- Identify areas of progress and remaining gaps
- Benchmark against industry standards and peer performance
- Update the roadmap based on findings
- Scaling Strategy
- Prioritize next implementation areas based on business impact
- Apply lessons from the pilot to streamline subsequent deployments
- Standardize approaches while allowing for site-specific adaptations
- Develop templates and playbooks for consistent implementation
- Continuous Improvement
- Refresh training and awareness programs regularly
- Evaluate new technologies that could enhance convergence
- Refine processes based on operational experience
- Adjust metrics and targets as capabilities mature
- Organizational Evolution
- Consider structural changes to formalize integration (e.g., unified teams)
- Develop career paths that value cross-domain expertise
- Align performance metrics and incentives with convergence goals
- Build succession plans that maintain critical knowledge
Practical Tip: "Document everything—not just technical configurations, but decision rationales, workarounds, and lessons learned. This institutional knowledge becomes invaluable as you scale and as team members change." – CIO, Discrete Manufacturing
Output: Regular progress reports, updated roadmap, and continuous improvement plan. This creates a sustainable approach to ongoing convergence.
Implementation tools and templates
To accelerate your implementation, consider these practical resources:
Success Metrics Scorecard

RACI Matrix Template
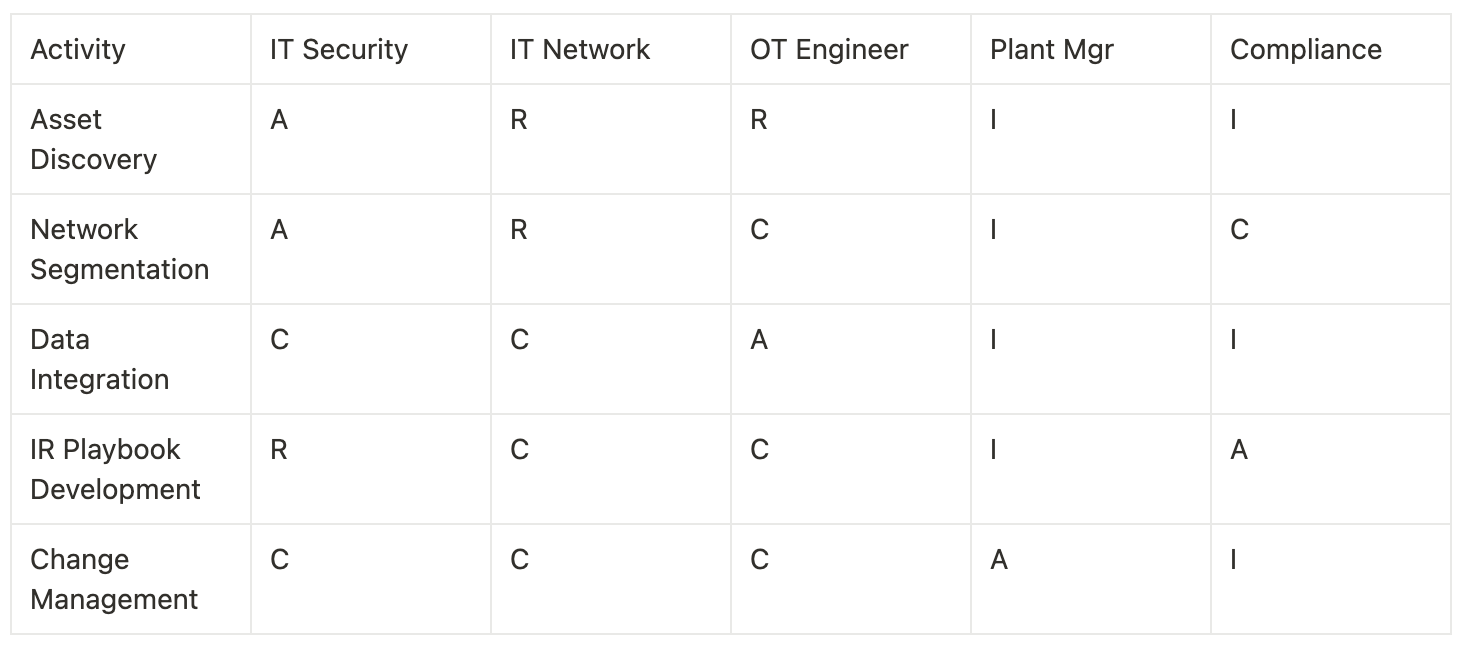
R=Responsible, A=Accountable, C=Consulted, I=Informed
Phased Implementation Roadmap

This framework provides a structured approach to OT/IT convergence that balances technical requirements with operational realities. By following these steps, you can achieve meaningful integration while minimizing risk to production, delivering tangible business value at each stage of the journey.
Remember that successful convergence isn't about forcing IT practices onto OT environments or vice versa. It's about creating appropriate integration points that respect the legitimate requirements of both domains while enabling the data flows and security controls necessary for modern manufacturing.
Why this framework works
This framework works because it respects the dual reality you face every day as a manufacturing IT leader. It's not about imposing IT standards on OT systems or compromising production reliability for theoretical security benefits.
Instead, it creates a practical middle path that delivers measurable value while acknowledging real-world constraints. By starting with visibility and building toward integration, you're addressing your responsibility to protect operations while creating the foundation for data-driven improvements.
Technology integration fails without cultural alignment. The cross-functional teams, RACI matrix, and communication protocols create the human infrastructure necessary for sustainable integration.
Meanwhile, the pilot-first approach allows you to validate your methods before broader deployment, reducing risk and building credibility with operations teams. Each phase generates tangible outcomes—from increased asset visibility and reduced downtime to improved OEE and streamlined compliance—connecting technical work to business priorities that executives understand and value.
OT/IT convergence is a fundamental shift in how manufacturing technology enables business success. The organizations that thrive in the coming decade will be those that successfully integrate their operational and information technologies.
This framework gives you the roadmap to lead that integration, balancing immediate operational needs with strategic transformation, technical requirements with human factors, and security imperatives with business innovation. Your role as a manufacturing IT leader has never been more challenging or more critical. With this practical approach, you can turn that challenge into an opportunity to drive significant value for your organization.
FAQ
1. Why is IT/OT integration so challenging in manufacturing environments?
Manufacturing IT/OT integration is difficult due to legacy systems with long lifecycles, incomplete documentation, and tight interdependencies. Any change risks cascading failures. These environments were never designed for connectivity or modern security, making safe upgrades complex and risky.
2. What’s the operational-security paradox in manufacturing IT?
Manufacturers must connect systems for efficiency but also isolate them for security. Production demands uptime, while security demands isolation—yet converged IT/OT networks are now the top ransomware target, and downtime is extremely expensive. Retrofitting security into old OT systems is a major challenge.
3. How does IT/OT convergence improve manufacturing operations?
Convergence enables real-time data integration, predictive maintenance, and unified monitoring. This leads to 15–20% higher equipment effectiveness, up to 30% less unplanned downtime, and faster repairs—directly boosting capacity, reliability, and cost savings.
4. What steps should manufacturing IT leaders take to start OT/IT convergence?
Begin with a comprehensive asset and network assessment, assemble a cross-functional team, set measurable business-aligned KPIs, pilot on a critical line or plant, and establish a continuous improvement cycle. Use tools like RACI matrices and phased roadmaps to manage risk and drive progress.
5. How does OT/IT convergence impact compliance and cybersecurity?
Convergence enhances compliance by enabling automated documentation, consistent policy enforcement, and easier audits. It also improves security by providing unified visibility and coordinated incident response across both IT and OT domains, reducing blind spots and risk.